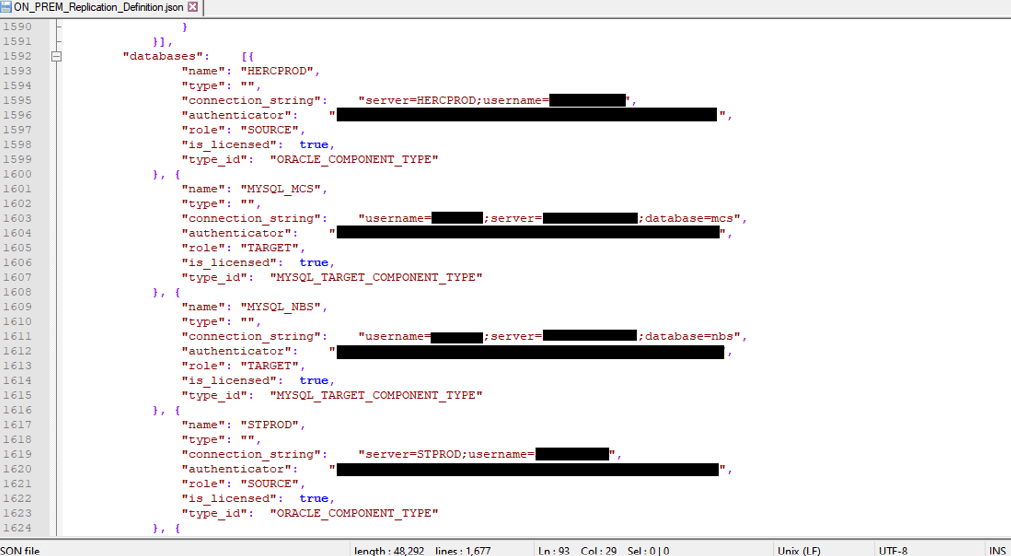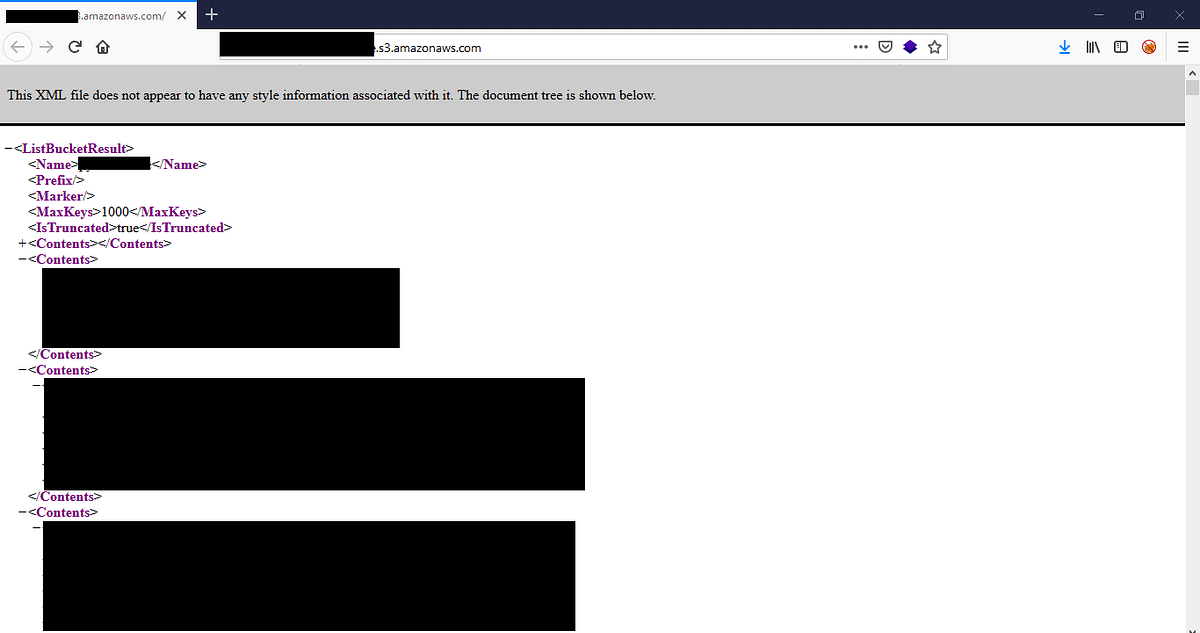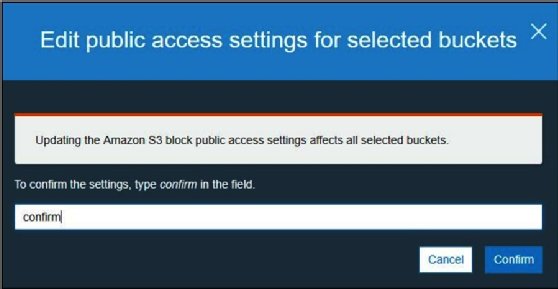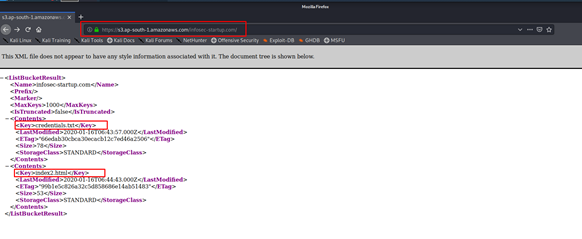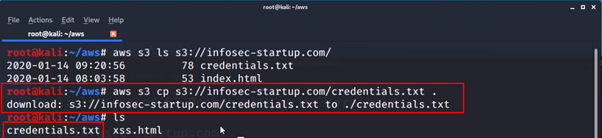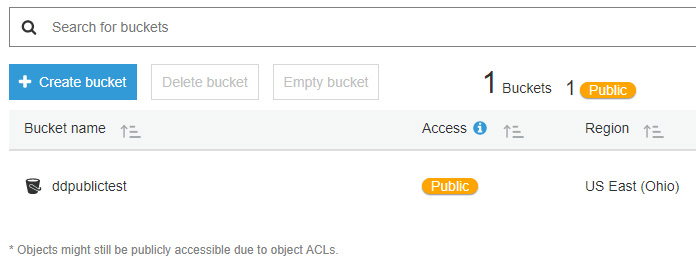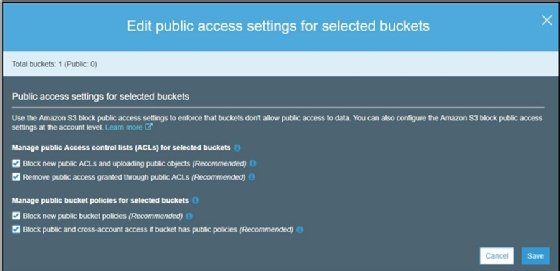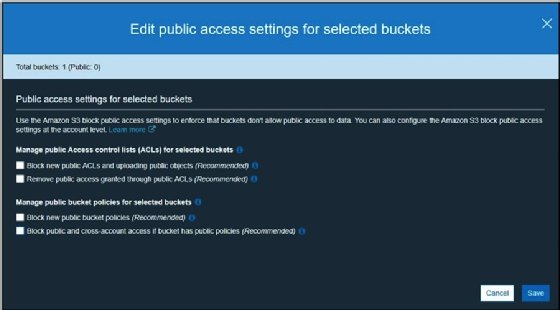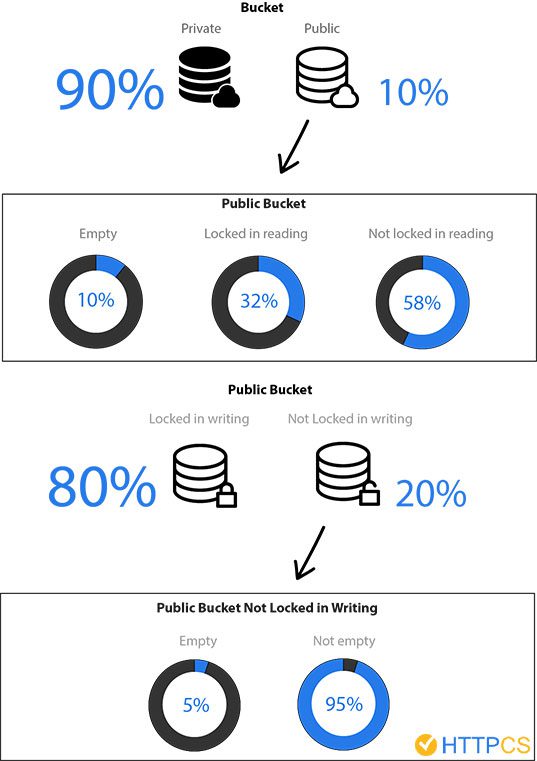
2% of Amazon S3 public buckets are unprotected, lead to data corruption attacks, malware spreading, and ransomware attacks • Penetration Testing

Amazon S3 Block Public Access – Another Layer of Protection for Your Accounts and Buckets | AWS News Blog

Strengthen the security of sensitive data stored in Amazon S3 by using additional AWS services | AWS Security Blog